Critical Unauthenticated Local File Inclusion Vulnerability in WP Ghost Plugin fixed
Cybersecurity
Man-in-the-Middle (MITM) Attacks
Posted by
admin on
2025-04-03 13:09:19 |
Share: Facebook |
Twitter |
Whatsapp |
Linkedin Visits:
590
Critical Unauthenticated Local File Inclusion Vulnerability in WP Ghost Plugin Fixed
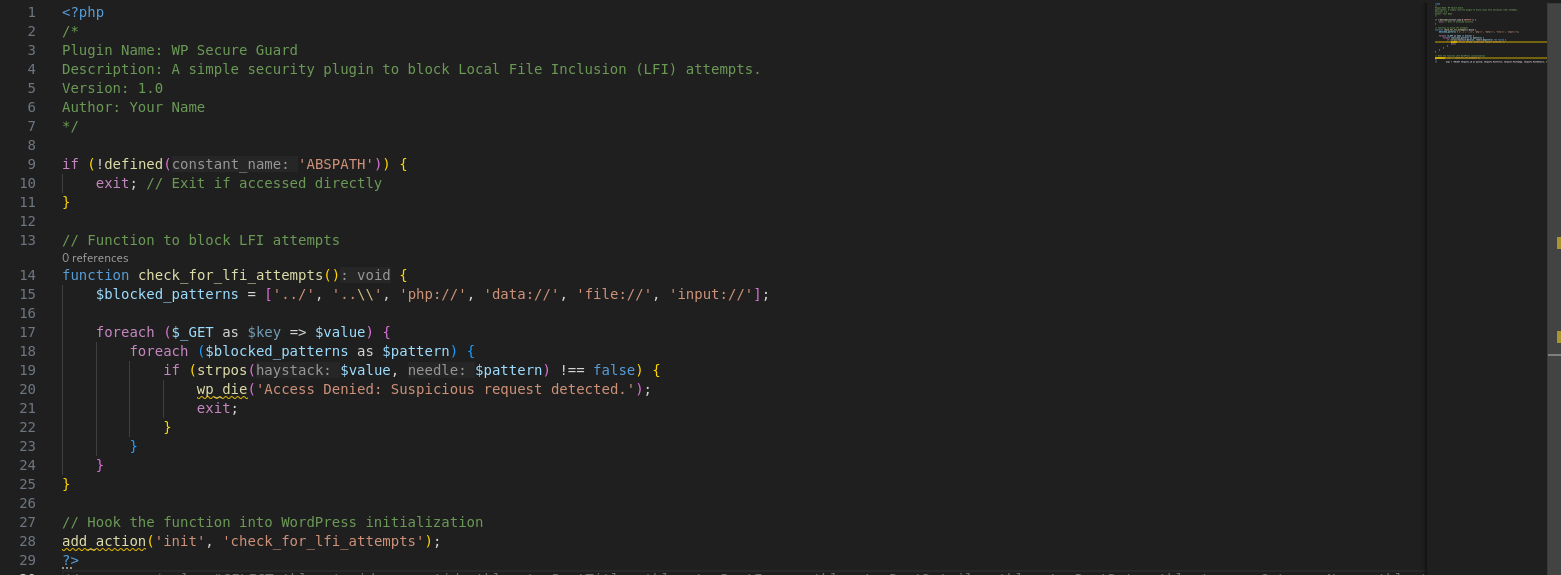
A critical vulnerability was discovered in the WP Ghost WordPress plugin, which exposed websites to potential remote code execution (RCE) attacks. The flaw, identified as CVE-2024-26909, arose due to insufficient user input validation via the URL path, which could be exploited for Local File Inclusion (LFI). This vulnerability affected all versions of WP Ghost up to 5.4.01 and had received a high Common Vulnerability Scoring System (CVSS) score of 9.6, indicating severe risk.
Vulnerability Details
The vulnerability occurred when an attacker manipulated the URL path to include arbitrary files. This could lead to unauthorized access to sensitive files on the server and, in some cases, remote code execution. However, the issue only affected sites where the "Change Paths" feature was set to either Lite or Ghost mode. By default, this setting was disabled, reducing the risk for some users.
Patch and Mitigation
The vulnerability was reported in late February 2024, and the WP Ghost development team swiftly addressed the issue by releasing a patched version, WP Ghost 5.4.02, within a week. Users were strongly urged to update their WP Ghost plugin to the latest version to secure their websites against potential exploits.
To mitigate the risk, users were advised to:
-
Update WP Ghost to version 5.4.02 or later to patch the vulnerability.
-
Enable automatic updates to ensure that future security patches were applied promptly.
-
Review plugin settings to confirm whether the "Change Paths" feature was enabled in Lite or Ghost mode and disable it if not required.
-
Conduct security audits on installed plugins to identify any pending updates that required manual intervention.
Importance of Regular Security Updates
WP Ghost is a popular security plugin with over 200,000 active installations, offering protection against threats such as SQL injection, script injection, vulnerability exploitation, malware attacks, file inclusion exploits, directory traversal attacks, and cross-site scripting (XSS). This incident underscored the importance of maintaining updated software to mitigate security risks effectively.
Website administrators were encouraged to remain vigilant and proactive in managing WordPress security by:
-
Keeping WordPress core, themes, and plugins updated.
-
Using web application firewalls (WAFs) to block exploit attempts.
-
Regularly backing up website data to ensure quick recovery in case of an attack.
By promptly addressing this security flaw, website owners were able to safeguard their sites against unauthorized access and potential data breaches. If you are unsure about your website's security status, consider consulting a cybersecurity expert or using a security plugin to conduct a thorough security scan.
For more information, visit WP Ghost's official website or the WordPress Plugin Repository for the latest updates and recommendations.